tricky.lnk – Unicode Text Spoofing
by admin
Tuesday, November 8th, 2016 at 3:20 pm

Bidirectional Unicode spoofing is not a new concept, malware has been using the technique for the last decade, but I was toying around with unicode earlier today for a phishing engagement, by default Win7 doesn’t allow you to create filenames with unicode chars unless you:
-
a. Open RegEdit
b. Navigate to HKey_Current_User/Control Panel/Input Method
c. Set REG_SZ “EnableHexNumpad” to be “1” (If there is no EnableHexNumpad, then add it and set its value to 1).
d. Reboot your system.
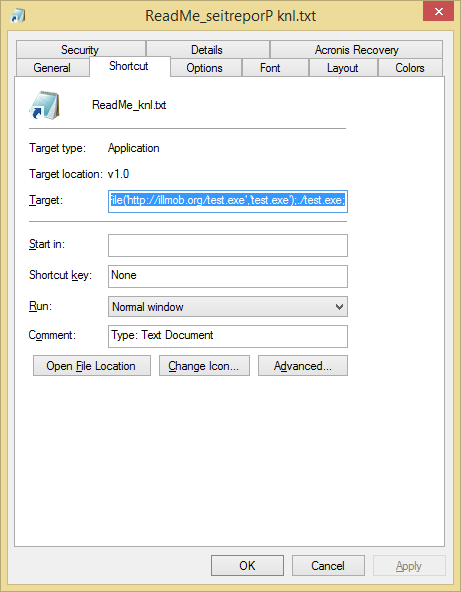
I didnt want to do this so I created a .vbs script that creates a .lnk file that spoofs the file extension with Unicode chars. This allows you to reverse the “.lnk” file extension, append “.txt” to the end and change the icon to notepad.exe’s icon to make it appear as a text file. When executed, the Target payload is a powershell webdl and execute.
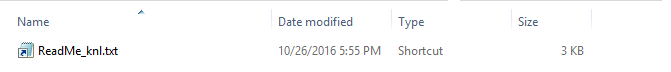
This technique utlizes Right-to-Left Override [RLO] This trick uses the fact that some languages are being written from right side towards left. A Unicode character was created to support such languages. It displaces the displayed extension in reverse order ( i.e. blah.lnk becomes blahknl. ). This character code is: U+202e more information on this character ::here::. This doesn’t just apply to .lnk , you can do this trick with .exe, .com, .pif, .scr etc… files.
You can find the .vbs code on my GitHub ::here::
How-To: Download the .vbs file and edit the download url to point to your own payload. save the .vbs and execute it. The file named “ReadMe_knl.txt” will be created on your desktop. Send that to phishing target. May need to obfuscate further to bypass email security appliances.
To-Do: Make a script that allows you to choose whatever filename/extension you type and work on different payloads besides webdl.
BONUS: Created a PowerShell script to do the same thing that the vbs script does, although for some reason it hides the reversed ‘lnk’ from the filename